In a world where cybersecurity incidents are constant, the challenge is no longer just identifying threats—it’s ensuring that teams focus on the right ones. Poorly tuned alerts lead to fatigue, missed critical incidents, and slower response times. Optimising alerts and incident reporting is crucial for enabling teams to prioritise and act swiftly on what matters most.
For organisations operating under NIS 2 and DORA, effective incident management is a core requirement. Clear, actionable alerts not only improve operational efficiency but also ensure compliance with incident response protocols.
Why Optimised Alerts Matter
Overwhelming teams with alerts creates a dangerous cycle:
- High-priority incidents may be overlooked in the noise.
- False positives erode trust in the system, leading to slower response times.
- Teams waste time triaging irrelevant or duplicate alerts.
A streamlined alerting system ensures critical issues are prioritised, enabling faster remediation and minimising the impact of vulnerabilities or attacks.
How Aqua CNAPP Improves Alert Management
-
Customise Alert Thresholds:
- Use Aqua’s alerting configurations to filter out low-severity incidents.
- Focus on critical vulnerabilities, misconfigurations, and active threats in production environments.
-
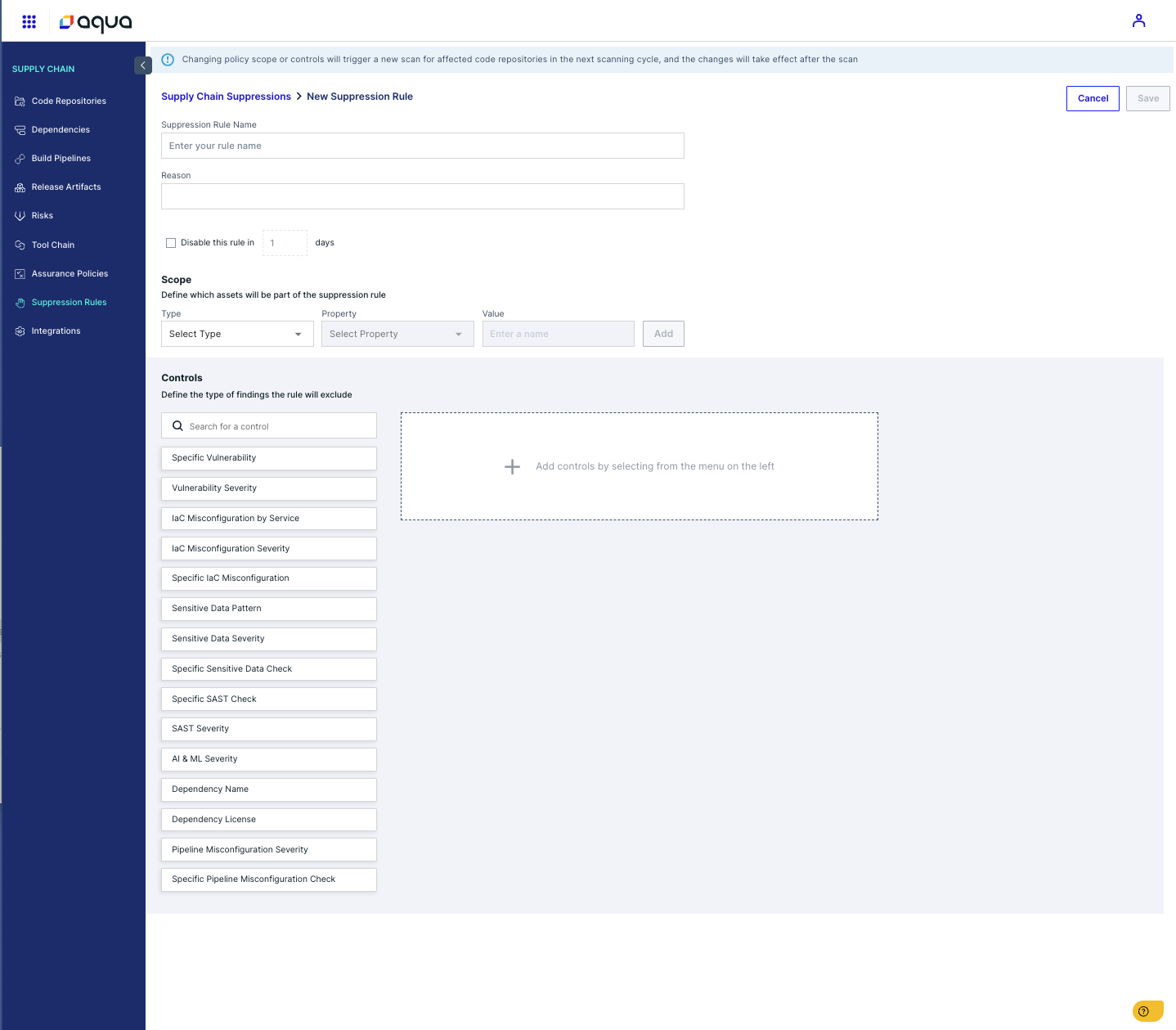
Leverage Suppressions:
- Suppress known false positives or irrelevant alerts while maintaining visibility in reports for audit purposes.
- Configure suppressions based on resource type, region, or specific plugin tests.
-
Integrate with SIEM:
- Connect Aqua’s incident notifications to your SIEM platform for centralised management.
- Use automation to categorise and escalate incidents based on severity.
-
Monitor and Refine Alerts:
- Regularly review alert configurations to adapt to evolving workloads and environments.
- Use Aqua’s analytics to identify trends in alert frequency and refine policies accordingly.
Practical Example: Configuring Critical Alerts
Aqua’s alert dashboard allows teams to:
- Highlight new vulnerabilities introduced by pipeline activity.
- Prioritise runtime threats such as malware or privilege escalation attempts.
- Suppress low-priority findings, such as benign misconfigurations in non-production environments.
By narrowing the focus, teams are equipped to respond more effectively to incidents that pose genuine risks.


Summary
Optimised alerting is not just a matter of convenience—it’s a necessity for maintaining resilience in the face of evolving cyber threats. Aqua’s flexible configurations ensure that your teams focus on the right issues, improving response times and reducing fatigue. With streamlined incident reporting, organisations can meet NIS 2 and DORA requirements while empowering their teams to perform at their best.

Leave a comment