While pre-deployment scanning is essential, runtime protection is the last line of defence. Once workloads are active, they become exposed to evolving threats like privilege escalations, fileless malware, and cryptomining attacks. Real-time monitoring and mitigation are crucial for safeguarding your production environment.
For organisations striving to meet DORA’s requirements for operational continuity, runtime protection provides the assurance needed to keep workloads secure and compliant.
Why Runtime Protection is Crucial
Cyber threats don’t stop once applications are deployed. Without runtime protection:
- Vulnerabilities in production environments remain exploitable.
- Unauthorised access or malicious behaviours can compromise workloads.
- Teams may miss opportunities to mitigate risks before they escalate.
How Aqua CNAPP Secures Workloads in Real Time
-
Deploying the Right Enforcers:
- Aqua Enforcer: Installed on VMs or Kubernetes nodes, offering the broadest capabilities.
- KubeEnforcer: Acts as an admission controller in Kubernetes clusters.
- MicroEnforcer: When you have reduced control plane access but still need to secure those container applications – think AWS Fargate workloads!
- NanoEnforcer: Embedded in serverless functions for environments like AWS Lambda. Note: The enforcer type dictates the controls available to you in the runtime policies.
-
Enabling Default Policies:
- Start with Aqua’s prebuilt runtime policies, which include controls for:
- Real-Time Malware Detection: Blocks known malicious signatures.
- Privilege Escalation Prevention: Stops workloads from running with unnecessary privileges.
- Reverse Shell Blocking: Prevents unauthorised access to workloads.
- Start with Aqua’s prebuilt runtime policies, which include controls for:
-
Transitioning from Alert to Enforce Mode:
- Begin in alert-only mode to monitor incidents without disrupting operations.
- Gradually move to enforce mode, blocking threats automatically once teams are confident in policy configurations.
-
Incident Reporting and Integration:
- Integrate Aqua with your SIEM platform to centralise incident reporting.
- Provide SOC teams with detailed alerts for rapid response.
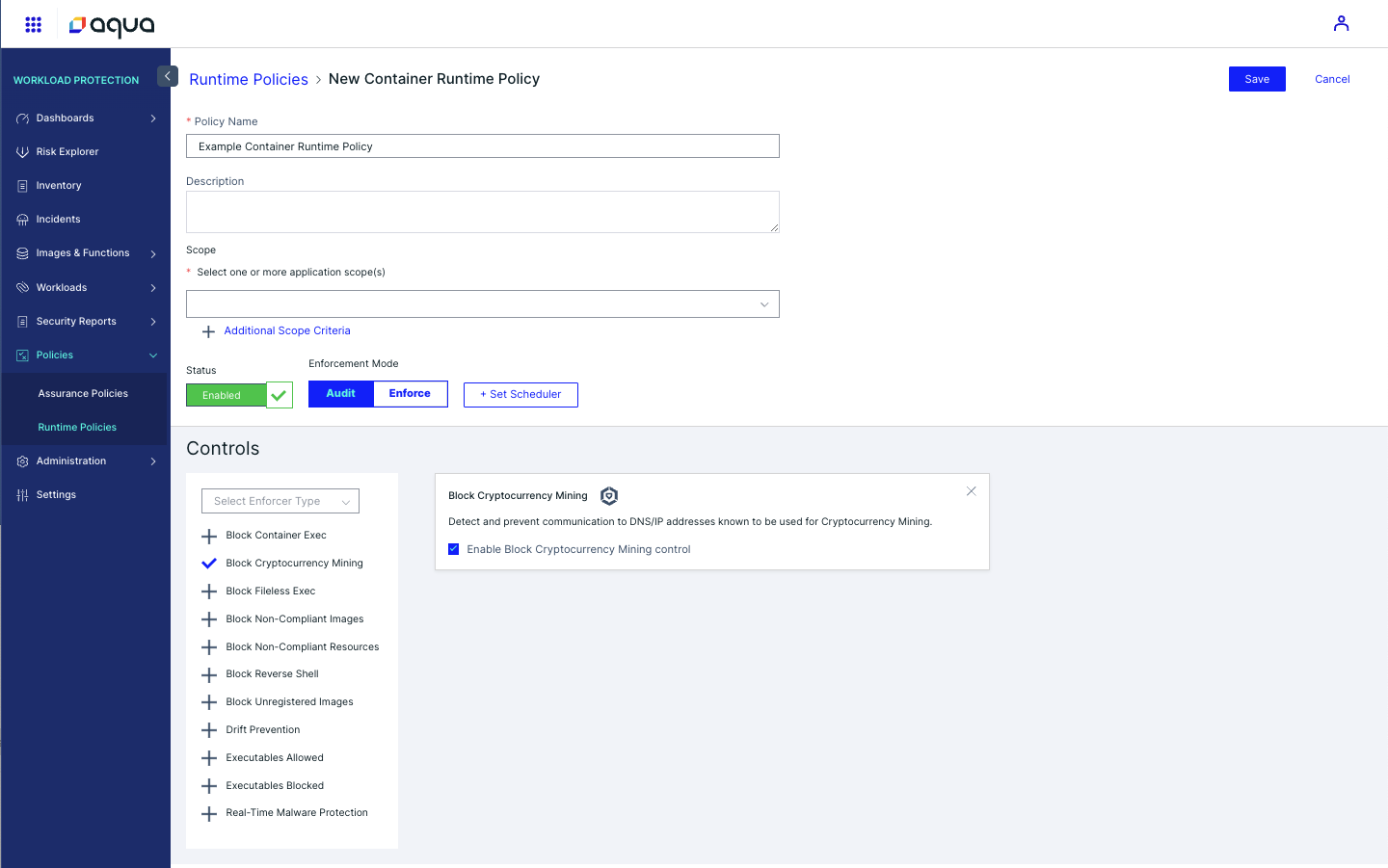
Practical Example: Real-Time Cryptomining Detection
Cryptomining is a common runtime threat. Aqua detects anomalies in CPU or memory usage, correlates them with known cryptomining patterns, and either alerts the SOC team or automatically blocks the workload, depending on the policy configuration.
Summary
Runtime protection is your safety net for active environments, providing the resilience demanded by DORA. Aqua’s enforcers and runtime policies ensure that even in the face of emerging threats, your workloads remain secure and compliant. With proactive monitoring and mitigation, production environments are no longer a blind spot—they’re a fortress.

Leave a comment